AWS
Connect Cased to AWS to manage and monitor your cloud infrastructure
Quick Connect (Recommended)
Section titled “Quick Connect (Recommended)”The fastest way to set up AWS access for Cased is using our CloudFormation template:
- Go to Cased - Navigate to https://app.cased.com/connections/aws
- Click Quick Connect AWS - This will launch the AWS Console with the template pre-filled
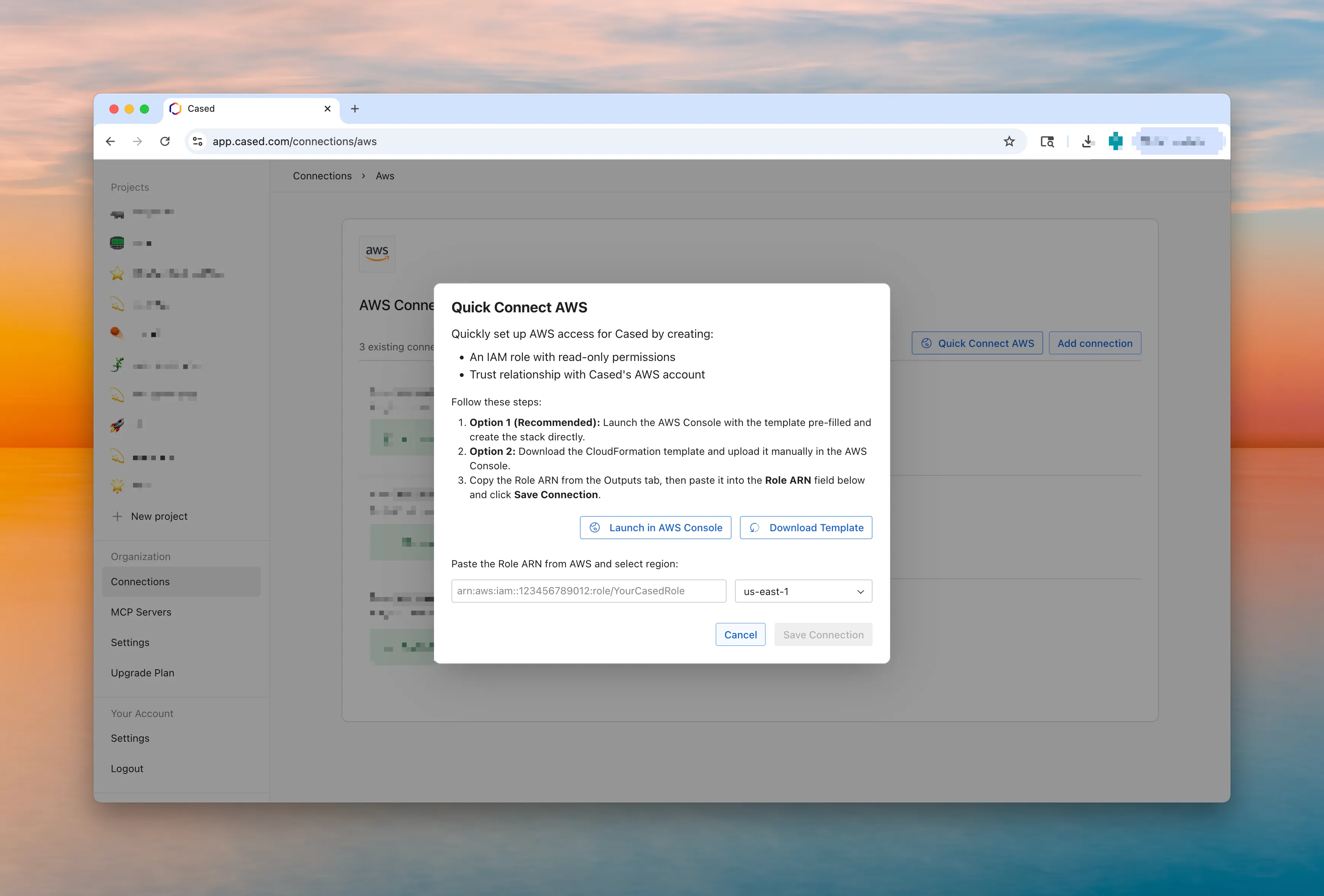
- Create the stack - Follow the CloudFormation wizard to create the stack
- Get the Role ARN - Copy the Role ARN from the Outputs tab after stack creation
- Configure Cased - Paste the Role ARN and select your region in Cased’s connection settings
CloudFormation Template
AWSTemplateFormatVersion: "2010-09-09"Description: "Cased Quick Connect - Creates IAM Role for AWS Infrastructure Scanning"
Parameters: RoleName: Type: String Default: CasedRole Description: Name of the IAM role that will be created
Resources: CasedInfraPolicy: Type: AWS::IAM::ManagedPolicy Properties: Description: Policy for Cased to scan AWS infrastructure PolicyDocument: Version: "2012-10-17" Statement: - Sid: VisualEditor0 Effect: Allow Action: - autoscaling:Describe* - cloudformation:Describe* - cloudformation:ListStacks - cloudfront:ListDistributions - cloudtrail:DescribeTrails - cloudtrail:GetTrail - cloudtrail:GetTrailStatus - cloudtrail:LookupEvents - cloudwatch:DeleteAlarms - cloudwatch:DescribeAlarmHistory - cloudwatch:DescribeAlarms - cloudwatch:DescribeAlarmsForMetric - cloudwatch:GetMetricData - cloudwatch:GetMetricStatistics - cloudwatch:GetMetricWidgetImage - cloudwatch:ListMetrics - cloudwatch:ListTagsForResource - cloudwatch:PutMetricAlarm - cloudwatch:TagResource - cloudwatch:UntagResource - dynamodb:DescribeTable - dynamodb:ListTables - ec2:DescribeInstances - ec2:DescribeNetworkInterfaces - ec2:DescribeSecurityGroups - ec2:DescribeSubnets - ec2:DescribeVpcs - ecs:DescribeClusters - ecs:DescribeServices - ecs:DescribeTaskDefinition - ecs:DescribeTasks - ecs:ListClusters - ecs:ListServices - ecs:ListTasks - ecr:DescribeRepositories - ecr:GetLifecyclePolicy - ecr:GetRegistryScanningConfiguration - ecr:GetRepositoryPolicy - ecr:ListImages - ecr:ListTagsForResource - eks:ListClusters - eks:DescribeCluster - eks:ListNodegroups - elasticache:Describe* - elasticache:ListTagsForResource - elasticbeanstalk:DescribeEnvironments - elasticloadbalancing:DescribeLoadBalancers - iam:GetPolicy - iam:GetPolicyVersion - iam:GetRole - iam:ListAttachedRolePolicies - iam:ListPolicies - iam:ListRoles - iam:ListUsers - kms:DescribeKey - kms:ListKeys - lambda:ListFunctions - logs:DescribeLogStreams - logs:DescribeLogGroups - logs:GetLogEvents - logs:FilterLogEvents - rds:DescribeDBInstances - rds:DescribeDBSnapshots - rds:DescribeEvents - rds:ListTagsForResource - s3:GetBucketLifecycleConfiguration - s3:GetBucketLocation - s3:GetBucketPublicAccessBlock - s3:GetBucketTagging - s3:GetBucketVersioning - s3:GetEncryptionConfiguration - s3:GetObject - s3:ListAllMyBuckets - s3:ListBucket - sns:CreateTopic - sns:GetTopicAttributes - sns:ListSubscriptions - sns:ListTopics - sns:Subscribe - sqs:ListQueues Resource: "*"
CasedInfraRole: Type: AWS::IAM::Role Properties: RoleName: !Ref RoleName Description: IAM role for Cased to work with AWS infrastructure AssumeRolePolicyDocument: Version: "2012-10-17" Statement: - Effect: Allow Principal: AWS: "arn:aws:iam::495860673956:root" Action: "sts:AssumeRole" ManagedPolicyArns: - !Ref CasedInfraPolicy
Outputs: RoleARN: Description: ARN of the created IAM role. Copy this value into Cased. Value: !GetAtt CasedInfraRole.ArnPulumi Setup
Section titled “Pulumi Setup”If you’re using Pulumi for infrastructure management, you can create the IAM role with this TypeScript code:
Pulumi TypeScript Example
import * as pulumi from "@pulumi/pulumi";import * as aws from "@pulumi/aws";
// Configurationconst config = new pulumi.Config();const roleName = config.get("roleName") || "CasedRole";
// Create the policy document for Cased infrastructure scanningconst casedInfraPolicyDocument = aws.iam.getPolicyDocument({ statements: [ { sid: "VisualEditor0", effect: "Allow", actions: [ "autoscaling:Describe*", "cloudformation:Describe*", "cloudformation:ListStacks", "cloudfront:ListDistributions", "cloudtrail:DescribeTrails", "cloudtrail:GetTrail", "cloudtrail:GetTrailStatus", "cloudtrail:LookupEvents", "cloudwatch:DeleteAlarms", "cloudwatch:DescribeAlarmHistory", "cloudwatch:DescribeAlarms", "cloudwatch:DescribeAlarmsForMetric", "cloudwatch:GetMetricData", "cloudwatch:GetMetricStatistics", "cloudwatch:GetMetricWidgetImage", "cloudwatch:ListMetrics", "cloudwatch:ListTagsForResource", "cloudwatch:PutMetricAlarm", "cloudwatch:TagResource", "cloudwatch:UntagResource", "dynamodb:DescribeTable", "dynamodb:ListTables", "ec2:DescribeInstances", "ec2:DescribeNetworkInterfaces", "ec2:DescribeSecurityGroups", "ec2:DescribeSubnets", "ec2:DescribeVpcs", "ecs:DescribeClusters", "ecs:DescribeServices", "ecs:DescribeTaskDefinition", "ecs:DescribeTasks", "ecs:ListClusters", "ecs:ListServices", "ecs:ListTasks", "ecr:DescribeRepositories", "ecr:GetLifecyclePolicy", "ecr:GetRegistryScanningConfiguration", "ecr:GetRepositoryPolicy", "ecr:ListImages", "ecr:ListTagsForResource", "eks:ListClusters", "eks:DescribeCluster", "eks:ListNodegroups", "elasticache:Describe*", "elasticache:ListTagsForResource", "elasticbeanstalk:DescribeEnvironments", "elasticloadbalancing:DescribeLoadBalancers", "iam:GetPolicy", "iam:GetPolicyVersion", "iam:GetRole", "iam:ListAttachedRolePolicies", "iam:ListPolicies", "iam:ListRoles", "iam:ListUsers", "kms:DescribeKey", "kms:ListKeys", "lambda:ListFunctions", "logs:DescribeLogStreams", "logs:DescribeLogGroups", "logs:GetLogEvents", "logs:FilterLogEvents", "rds:DescribeDBInstances", "rds:DescribeDBSnapshots", "rds:DescribeEvents", "rds:ListTagsForResource", "s3:GetBucketLifecycleConfiguration", "s3:GetBucketLocation", "s3:GetBucketPublicAccessBlock", "s3:GetBucketTagging", "s3:GetBucketVersioning", "s3:GetEncryptionConfiguration", "s3:GetObject", "s3:ListAllMyBuckets", "s3:ListBucket", "sns:CreateTopic", "sns:GetTopicAttributes", "sns:ListSubscriptions", "sns:ListTopics", "sns:Subscribe", "sqs:ListQueues", ], resources: ["*"], }, ],});
// Create the managed policy for Cased infrastructure scanningconst casedInfraPolicy = new aws.iam.Policy("CasedInfraPolicy", { description: "Policy for Cased to scan AWS infrastructure", policy: casedInfraPolicyDocument.then((doc) => doc.json),});
// Create the IAM role for Casedconst casedInfraRole = new aws.iam.Role("CasedInfraRole", { name: roleName, description: "IAM role for Cased to work with AWS infrastructure", assumeRolePolicy: JSON.stringify({ Version: "2012-10-17", Statement: [ { Effect: "Allow", Principal: { AWS: "arn:aws:iam::495860673956:root", }, Action: "sts:AssumeRole", }, ], }), managedPolicyArns: [casedInfraPolicy.arn],});
export const roleArn = casedInfraRole.arn;export const roleName_output = casedInfraRole.name;export const policyArn = casedInfraPolicy.arn;After running pulumi up, copy the roleArn output value and paste it into Cased’s AWS connection settings.
Manual Setup
Section titled “Manual Setup”If you prefer to set up the IAM role manually:
-
In your AWS Management Console go to the IAM service
-
Create IAM Policy under Policies create a new policy in the JSON editor.
-
Paste this JSON into the policy editor and name is
CasedPolicy.CasedPolicy {"Version": "2012-10-17","Statement": [{"Effect": "Allow","Action": ["autoscaling:Describe*","cloudformation:Describe*","cloudformation:ListStacks","cloudfront:ListDistributions","cloudtrail:DescribeTrails","cloudtrail:GetTrail","cloudtrail:GetTrailStatus","cloudtrail:LookupEvents","cloudwatch:DeleteAlarms","cloudwatch:DescribeAlarmHistory","cloudwatch:DescribeAlarms","cloudwatch:DescribeAlarmsForMetric","cloudwatch:GetMetricData","cloudwatch:GetMetricStatistics","cloudwatch:GetMetricWidgetImage","cloudwatch:ListMetrics","cloudwatch:ListTagsForResource","cloudwatch:PutMetricAlarm","cloudwatch:TagResource","cloudwatch:UntagResource","dynamodb:DescribeTable","dynamodb:ListTables","ec2:DescribeInstances","ec2:DescribeNetworkInterfaces","ec2:DescribeSecurityGroups","ec2:DescribeSubnets","ec2:DescribeVpcs","ecs:DescribeClusters","ecs:DescribeServices","ecs:DescribeTaskDefinition","ecs:DescribeTasks","ecs:ListClusters","ecs:ListServices","ecs:ListTasks","ecr:DescribeRepositories","ecr:GetLifecyclePolicy","ecr:GetRegistryScanningConfiguration","ecr:GetRepositoryPolicy","ecr:ListImages","ecr:ListTagsForResource","eks:ListClusters","eks:DescribeCluster","eks:ListNodegroups","elasticache:Describe*","elasticache:ListTagsForResource","elasticbeanstalk:DescribeEnvironments","elasticloadbalancing:DescribeLoadBalancers","iam:GetPolicy","iam:GetPolicyVersion","iam:GetRole","iam:ListAttachedRolePolicies","iam:ListPolicies","iam:ListRoles","iam:ListUsers","kms:DescribeKey","kms:ListKeys","lambda:ListFunctions","logs:DescribeLogStreams","logs:DescribeLogGroups","logs:GetLogEvents","logs:FilterLogEvents","rds:DescribeDBInstances","rds:DescribeDBSnapshots","rds:DescribeEvents","rds:ListTagsForResource","s3:GetBucketLifecycleConfiguration","s3:GetBucketLocation","s3:GetBucketPublicAccessBlock","s3:GetBucketTagging","s3:GetBucketVersioning","s3:GetEncryptionConfiguration","s3:GetObject","s3:ListAllMyBuckets","s3:ListBucket","sns:CreateTopic","sns:GetTopicAttributes","sns:ListSubscriptions","sns:ListTopics","sns:Subscribe","sqs:ListQueues"],"Resource": "*"}]} -
Create IAM Role
- Open IAM in AWS Console
- Go to Roles → Create role
- Choose “AWS account” as trusted entity type
- Enter Cased account ID:
495860673956 - Attach the policy you created
- Name the role (e.g.,
CasedRole)
-
Almost done! Configure Cased:
- Copy your Role ARN from the role summary page
- Format:
arn:aws:iam::<YOUR_ACCOUNT_ID>:role/CasedRole - Paste the ARN in Cased’s AWS connection settings
- Select your AWS region
CloudWatch Triggers (Beta)
Section titled “CloudWatch Triggers (Beta)”CloudWatch triggers allow agents to automatically execute when AWS CloudWatch alarms are triggered. This enables proactive incident response for infrastructure issues like high CPU usage, database connection limits, or application errors.
How It Works
Section titled “How It Works”- Create or Adopt Alarms - Use Cased’s agent to create new CloudWatch alarms or adopt existing ones
- SNS Topic - Cased automatically creates an SNS topic in your AWS account for alarm notifications
- Webhook Integration - The SNS topic subscribes to Cased’s webhook endpoint
- Agent Execution - When an alarm enters the ALARM state, your agent runs automatically
Required Permissions
Section titled “Required Permissions”The IAM policies above include the necessary permissions for CloudWatch triggers:
CloudWatch Alarm Management:
PutMetricAlarm- Create/update alarmsDeleteAlarms- Remove alarmsDescribeAlarms,DescribeAlarmsForMetric,DescribeAlarmHistory- List and inspect alarmsTagResource,UntagResource,ListTagsForResource- Tag alarms as Cased-managed
SNS Topic Management:
CreateTopic- Create notification topic for your organizationSubscribe- Subscribe Cased webhook to receive alarm notificationsGetTopicAttributes- Check if topic exists
Using CloudWatch Triggers
Section titled “Using CloudWatch Triggers”Once your IAM role has the required permissions:
- In Agents - Add a CloudWatch Alarm trigger when creating or editing an agent
- Via Chat - Ask Cased to create alarms for specific metrics (e.g., “Create an alarm for RDS CPU usage above 80%”)
- Adopt Existing - Connect existing CloudWatch alarms to Cased agents without modifying their settings
Security Considerations
Section titled “Security Considerations”- Alarm Ownership - Cased only deletes/updates alarms it created (tracked via
ManagedBy: Casedtag) - Organization Isolation - SNS topics include your organization ID to prevent cross-org access
- Webhook Authentication - All webhook requests are cryptographically signed and validated
- Least Privilege - Alarm management permissions are scoped to specific operations only
Feature Access
Section titled “Feature Access”CloudWatch triggers are in beta. Contact Cased support to enable this feature for your organization.